Secure SaaS Access
Secure access to SaaS applications for trusted users on verified devices, keeping users safe and productive.
Secure access to SaaS applications for trusted users on verified devices, keeping users safe and productive.
Employees depend on SaaS applications to stay productive across multiple locations and devices, but traditional, network-centric controls can’t enforce least-privilege or validate device posture, leaving sensitive data exposed. AppGate ZTNA secures SaaS access with identity- and device-driven policies that continuously evaluate risk and adapt in near real-time. Only verified users on trusted devices can connect to authorized applications, reducing exposure, preventing unauthorized access, and preserving a seamless user experience.

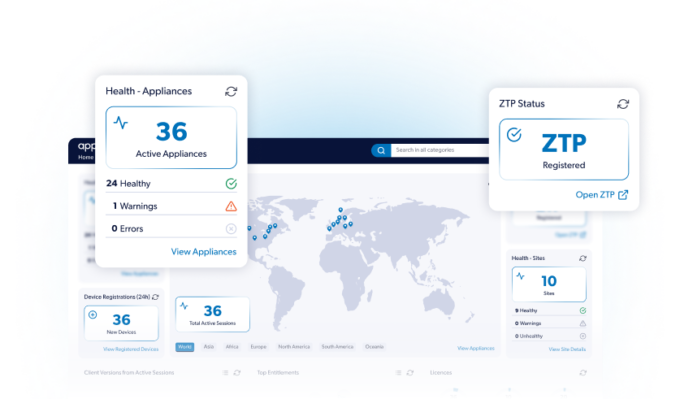
AppGate ZTNA simplifies secure access to SaaS applications by configuring risk rules, defining entitlements and monitoring compliance.
Implementing AppGate ZTNA for SaaS applications ensures secure, efficient and manageable access for trusted users and devices across the organization.
Get firsthand insights from our network security experts on the advantages of direct-routed ZTNA built for intricate hybrid IT environments. Each month features a different topic and live demo on how to strengthen security, control how data traverses your network, cut costs, and boost operational efficiencies.
