Secure OT/IoT Access
Protect access to OT and IoT networks without disrupting productivity or operations.
Protect access to OT and IoT networks without disrupting productivity or operations.
OT and IoT systems often rely on legacy protocols with minimal built-in protections, making secure access challenging without negatively impacting operations. AppGate ZTNA addresses this by cloaking critical control systems and enforcing identity- and policy-driven access, ensuring only authorized users and applications can communicate with sensors, controllers, and data collectors. This reduces exposure, prevents unauthorized access, and maintains operational efficiency.

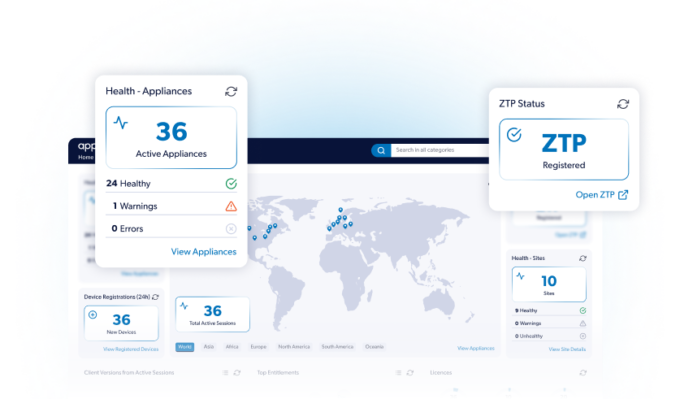
AppGate ZTNA simplifies the secure connection of OT and IoT environments by configuring connectors, defining policies, and monitoring traffic for optimal performance.
Implementing AppGate ZTNA for OT and IoT delivers secure, efficient, and manageable connectivity across complex and distributed environments.
Get firsthand insights from our network security experts on the advantages of direct-routed ZTNA built for intricate hybrid IT environments. Each month features a different topic and live demo on how to strengthen security, control how data traverses your network, cut costs, and boost operational efficiencies.
