Prove Zero Trust. Demonstrate Risk Reduction. Simplify audits.
Continuous, policy-driven access with board-ready evidence.
Continuous, policy-driven access with board-ready evidence.
Show measurable risk reduction without slowing the business.
Unified logs + real-time enforcement cut audit prep by up to 60%.
Segment-of-one access; Single Packet Authorization (SPA)-powered invisibility.
Distributed enforcement; no single cloud broker dependency.
Direct-routed paths avoid egress fees and vendor middle-mile.
AppGate ZTNA enables CISOs to prove the business impact of Zero Trust initiatives by aligning controls to board-level risk priorities, not just security operations.

Meet requirements. Prove Compliance. Reduce Audit Fatigue
Fewer places to attack; fewer chances to move laterally.
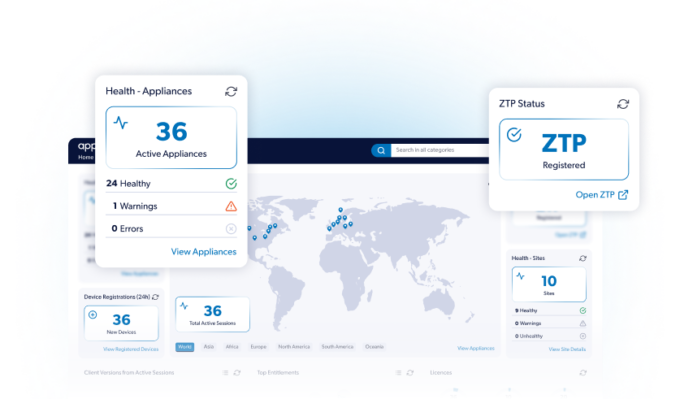
Validated outcomes in regulated environments.