The rise of remote workforces and hybrid work environments led organizations to quickly implement secure remote access solutions that enabled their teams to keep working throughout the pandemic ... and now going forward into the future. Zero Trust Network Access (ZTNA) has emerged as the best option for modern organizations, protecting attack vectors that legacy remote access security solutions like VPNs have historically left vulnerable.
According to Verizon’s 2022 Data Breach Investigations Report, use of stolen credentials is the leading technique in breaches, which amplifies the importance of remote access security. Using Zero Trust principles in secure remote access solutions has proven to be highly effective and is predicted to grow more popular. Gartner forecasts that 40% of remote access security will be serviced by ZTNA solutions by 2024, up from only 5% in 2020.
Today’s remote access security challenges
Legacy remote access security solutions aren’t secure enough, can’t scale fast enough nor were they designed with today’s sophisticated threat actors in mind. They don’t securely connect users to resources for the new way that work gets done. Some remote access security challenges include:
- Distributed workforce: Your attack surface grows when more users are connecting from more locations.
- Distributed workloads: Accessing resources in the cloud or in data centers creates more connections and adds complexity to policy enforcements and entitlements.
- Human error: According to Verizon’s report, 82% of breaches over the past year “involved the human element” like stolen credentials, phishing, misuse and other errors.
Remote access security risks
Connectivity isn’t just about one network anymore. Users are looking to gain access to dispersed resources that are on premises, in data centers and in the cloud. This adds complexity to remote access security and the best secure remote access solutions account for each use case and address all risks, including:
- Overly broad access: Legacy solutions don’t add context to their analysis for granting access, which typically means users have more permissions than they need.
- Cloud access: Shared responsibility between cloud providers and users creates complexity for cloud security and each cloud requires different and disparate controls.
- Bring Your Own Device (BYOD) policies: Much like the distributed workforce, this expands your attack surface. A report last year showed that 82% of organizations allow BYOD policies to some extent.
- Third-party access: Key business partners need access to resources, but also present a security risk. A 2021 Ponemon Institute report cites that 51% of data breaches are caused by third parties.
Secure remote access solutions
Not all secure remote access solutions are created equal. ZTNA can protect your crown jewels better than legacy solutions and can reduce your attack surface. Built on the principles of Zero Trust security, ZTNA is growing more influential across the cybersecurity landscape. The U.S. government adopted Zero Trust via an executive order, and many in the private sector are following suit. According to a Forrester survey, 68% of respondents’ organizations plan to increase their Zero Trust investments.
Using Zero Trust security principles has proven to make organizations more resilient. According to Ponemon’s 2021 Cost of a Data Breach Report, organizations that deployed mature Zero Trust programs reduced the average cost of a breach by $1.76 million compared to organizations that do not adhere to Zero Trust.
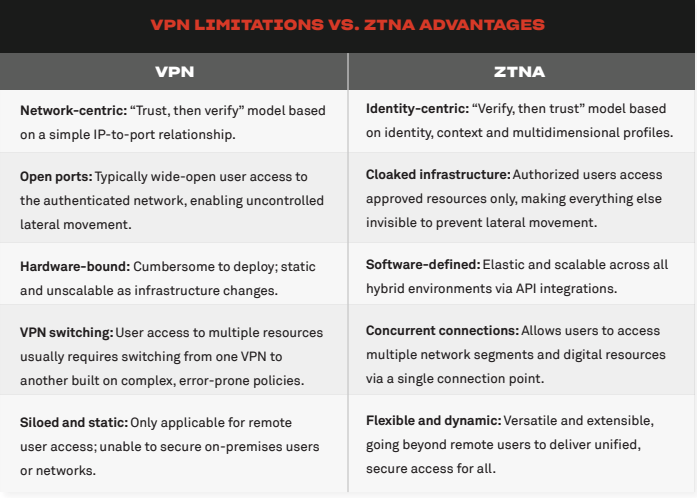
How to protect against remote access security issues
ZTNA brings agility to remote access security because it can scale, secure the cloud, is identity-centric rather than network-centric, provides least privilege access and takes a “default deny” rather than “default allow” approach to access.
ZTNA continuously monitors connections instead of the single authentication events that legacy solutions offer. If the context of a user or resource changes, privileges may adjust or be revoked. The user’s role, device’s security posture, geographic location and time that access is requested are just some of the conditions that ZTNA considers when determining whether access shall be granted. Without these contextual factors being evaluated, remote access security is at risk.
Benefits of secure remote access solutions
There are many advantages to ZTNA over other secure remote access solutions, such as agility, scalability and the fact that it’s built on the principle of least privilege access. Cloaking an organization’s infrastructure is another major benefit and an aspect of ZTNA that helps reduce the attack surface. This makes all resources and workloads invisible to any user that isn’t authenticated and authorized, keeping the threat actors out.
In addition, legacy remote access security solutions weren’t meant for the cloud, which is where most organizations are heading. ZTNA can assist a cloud migration because it scales like the cloud and uses a unified policy model to reduce the need for manual entitlements.
ZTNA also empowers DevOps teams to become DevSecOps by allowing concurrent access to multiple cloud environments and securing access to sessions rather than the whole network. This has been a game changer not just for access but also speeding up continuous integration/continuous delivery (CI/CD) pipelines.
In fact, Ponemon Institute’s Global Study on Zero Trust Security for the Cloud states that “implementing Zero Trust security methods doesn’t just safeguard hybrid cloud environments, but actually enables—and likely even accelerates—cloud transformation.”
How to evaluate secure remote access solutions and vendors
The cybersecurity landscape is flooded with vendors and solutions, but not all of them will be right for you. Consider your use case to determine what features you need as you sift through the many secure remote access solutions on the market.
Key capabilities to consider are the ZTNA vendor’s platform (whether it is a product or service), connectivity (agent-based or agentless) and the ascertaining the level of visibility and control that is offered by the vendor.
Appgate: A leader in secure remote access solutions
A report by global research firm Nemertes revealed that Appgate SDP, an industry-leading ZTNA solution, accelerated digital transformation initiatives by an average of 119% and was rated 9.5 out of 10 as being “most strategic to Zero Trust.”
Appgate SDP delivers remote access security with a reduced attack surface, simple administration and improved user experience so that users can connect from anywhere and any device to anything at any time.
Learn more about how Appgate SDP stands out among other secure remote access solutions by signing up for a weekly demo, available live each Wednesday.
Additional remote access security resources
eBook: 5-Step Guide to Simplify VPN to ZTNA Migration
eBook: Securing the Hybrid Enterprise
Blog: How to Sort and Select Vendors to Achieve Comprehensive Zero Trust Access