Secure Remote Access
Secure, seamless access for users to business-critical applications and services, anywhere, without exposing your network.
Secure, seamless access for users to business-critical applications and services, anywhere, without exposing your network.
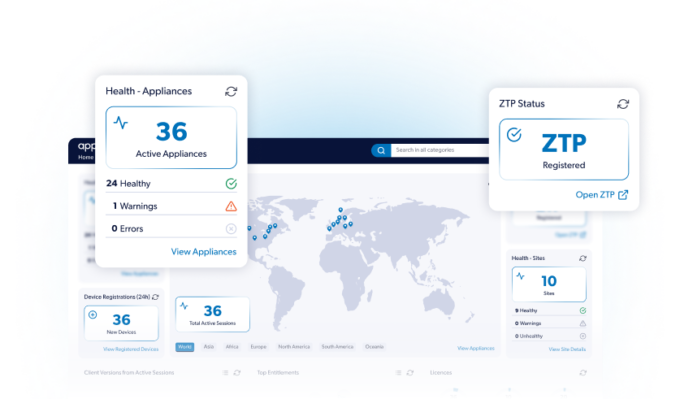
Traditional VPNs and perimeter-based security tools create unnecessary risk by granting broad network access, enabling lateral movement, data leakage, and compliance gaps. AppGate ZTNA secures hybrid IT environments by applying Zero Trust principles at the user and service level, ensuring only authorized individuals on approved devices can access specific services. This approach reduces the attack surface, enforces least-privilege access, and delivers high-performance, direct connections without routing traffic through cloud chokepoints.

AppGate ZTNA makes it easy to secure user-to-service access by quickly configuring identity providers, defining policies, and deploying clients without disrupting operations.
Implementing AppGate ZTNA delivers measurable security, operational, and user experience improvements across your organization.
Get firsthand insights from our network security experts on the advantages of direct-routed ZTNA built for intricate hybrid IT environments. Each month features a different topic and live demo on how to strengthen security, control how data traverses your network, cut costs and boost operational efficiencies.
